(1). 为什么研究VPN
用K8S后,为了解决开发环境联调问题,所以,才会研究下VPN(当然,还有其它的解决方案,比如:阿里针对K8S研发了类似的工具:KT Connect/SSH隧道).
注意:请合理运用工具去做正当的事情.
(2). L2TP介绍
VPN(Virtual Private Network,即”虚拟私人网络”)是一种通过在数据传输过程中加密的方式来保障数据传输安全的通信方式,L2TP是其中的一种加密方式.
(3). 环境验证
# 1. 查看操作系统版本
[root@vpn-server ~]# cat /etc/redhat-release
CentOS Linux release 7.9.2009 (Core)
# 2. 查看是否支持:pptp,返回结果为yes就表示通过:
[root@vpn-server ~]# modprobe ppp-compress-18 && echo yes
yes
# 3. 查看是否开启了TUN,返回结果为:File descriptor in bad state就表示通过.
[root@vpn-server ~]# cat /dev/net/tun
cat: /dev/net/tun: File descriptor in bad state
(4). 安装依赖
# ppp : 提供用户名密码验证功能,实现VPN的用户账号密码验证.
# libreswan : 提供IPsec功能,加密IP数据包.
# xl2tpd : 提供VPN功能,依赖于ppp和libreswan.
# 安装EPEL源,因为CentOS7官方源中已经去掉了xl2tpd.
[root@vpn-server ~]# yum install -y epel-release
[root@vpn-server ~]# yum -y update
# 安装xl2tpd和libreswan(libreswan用以实现IPSec,原先的openswan已经停止维护)
[root@vpn-server ~]# yum install -y xl2tpd libreswan lsof
(5). 配置(/etc/xl2tpd/xl2tpd.conf)
[global]
listen-addr = 0.0.0.0
ipsec saref = yes
[lns default]
ip range = 10.211.55.180-10.211.55.200 # 分配的IP池
local ip = 10.211.55.100 # 本机的IP地址(我宿主机的IP地址就是这个)
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxVPNserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
(6). 配置(/etc/ppp/options.xl2tpd)
ipcp-accept-local
ipcp-accept-remote
ms-dns 8.8.8.8
ms-dns 114.114.114.114
name xl2tpd
noccp
auth
# crtscts
idle 1800
mtu 1410
mru 1410
nodefaultroute
debug
# lock
proxyarp
connect-delay 5000
refuse-pap
refuse-chap
refuse-mschap
require-mschap-v2
persist
logfile /var/log/xl2tpd.log
(7). 配置(/etc/ipsec.conf)
config setup
protostack=netkey
dumpdir=/var/run/pluto/
virtual_private=%v4:10.0.0.0/8,%v4:172.100.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
include /etc/ipsec.d/*.conf
(8). 配置(/etc/ipsec.d/l2tp-ipsec.conf)
conn L2TP-PSK-NAT
rightsubnet=0.0.0.0/0
dpddelay=10
dpdtimeout=20
dpdaction=clear
forceencaps=yes
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=10.211.55.100 # 本机IP地址(我的宿主机IP地址就是这个)
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
(9). 设置用户名和密码(/etc/ppp/chap-secrets)
# 说明:用户名[空格]service[空格]密码[空格]指定IP
# Secrets for authentication using CHAP
# client server secret IP addresses
test * 888888 *
(10). 设置PSK(/etc/ipsec.d/default.secrets)
0.0.0.0 %any: PSK "test"
(11). CentOS7防火墙设置
# 在阿里云上要开防火墙,并把:安全出组/内网入方向规则添加(1701/4500)
# [root@vpn-server ~]# systemctl start firewalld
[root@vpn-server ~]# firewall-cmd --permanent --add-service=ipsec
[root@vpn-server ~]# firewall-cmd --permanent --add-port=1701/udp
[root@vpn-server ~]# firewall-cmd --permanent --add-port=4500/udp
[root@vpn-server ~]# firewall-cmd --permanent --add-masquerade
[root@vpn-server ~]# firewall-cmd --reload
(12). IP_FORWARD设置(/etc/sysctl.d/60-sysctl_ipsec.conf)
net.ipv4.ip_forward = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.eth0.accept_redirects = 0
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.conf.eth0.send_redirects = 0
net.ipv4.conf.eth1.accept_redirects = 0
net.ipv4.conf.eth1.rp_filter = 0
net.ipv4.conf.eth1.send_redirects = 0
net.ipv4.conf.eth2.accept_redirects = 0
net.ipv4.conf.eth2.rp_filter = 0
net.ipv4.conf.eth2.send_redirects = 0
net.ipv4.conf.ip_vti0.accept_redirects = 0
net.ipv4.conf.ip_vti0.rp_filter = 0
net.ipv4.conf.ip_vti0.send_redirects = 0
net.ipv4.conf.lo.accept_redirects = 0
net.ipv4.conf.lo.rp_filter = 0
net.ipv4.conf.lo.send_redirects = 0
net.ipv4.conf.ppp0.accept_redirects = 0
net.ipv4.conf.ppp0.rp_filter = 0
net.ipv4.conf.ppp0.send_redirects = 0
重启生效
[root@vpn-server ~]# systemctl restart network
(13). ipsec启动&检查
[root@vpn-server ~]# systemctl enable ipsec
[root@vpn-server ~]# systemctl restart ipsec
# 根据需要设置(ipsec verify检查不通过的情况下,再设置这个)
# virbr0 为你的网卡(ens192)
# [root@vpn-server ~]# echo 0 > /proc/sys/net/ipv4/conf/virbr0/rp_filter
# [root@vpn-server ~]# echo 0 > /proc/sys/net/ipv4/conf/virbr0-nic/rp_filter
[root@vpn-server ~]# ipsec verify
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 3.25 (netkey) on 3.10.0-1160.el7.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Two or more interfaces found, checking IP forwarding [OK]
Checking rp_filter [OK]
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OBSOLETE]
003 WARNING: using a weak secret (PSK)
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPS [OK]
Checking for obsolete ipsec.conf options [OK]
(14). xl2tpd启动
[root@vpn-server ~]# systemctl enable xl2tpd
[root@vpn-server ~]# systemctl restart xl2tpd
[root@vpn-server ~]# systemctl status xl2tpd
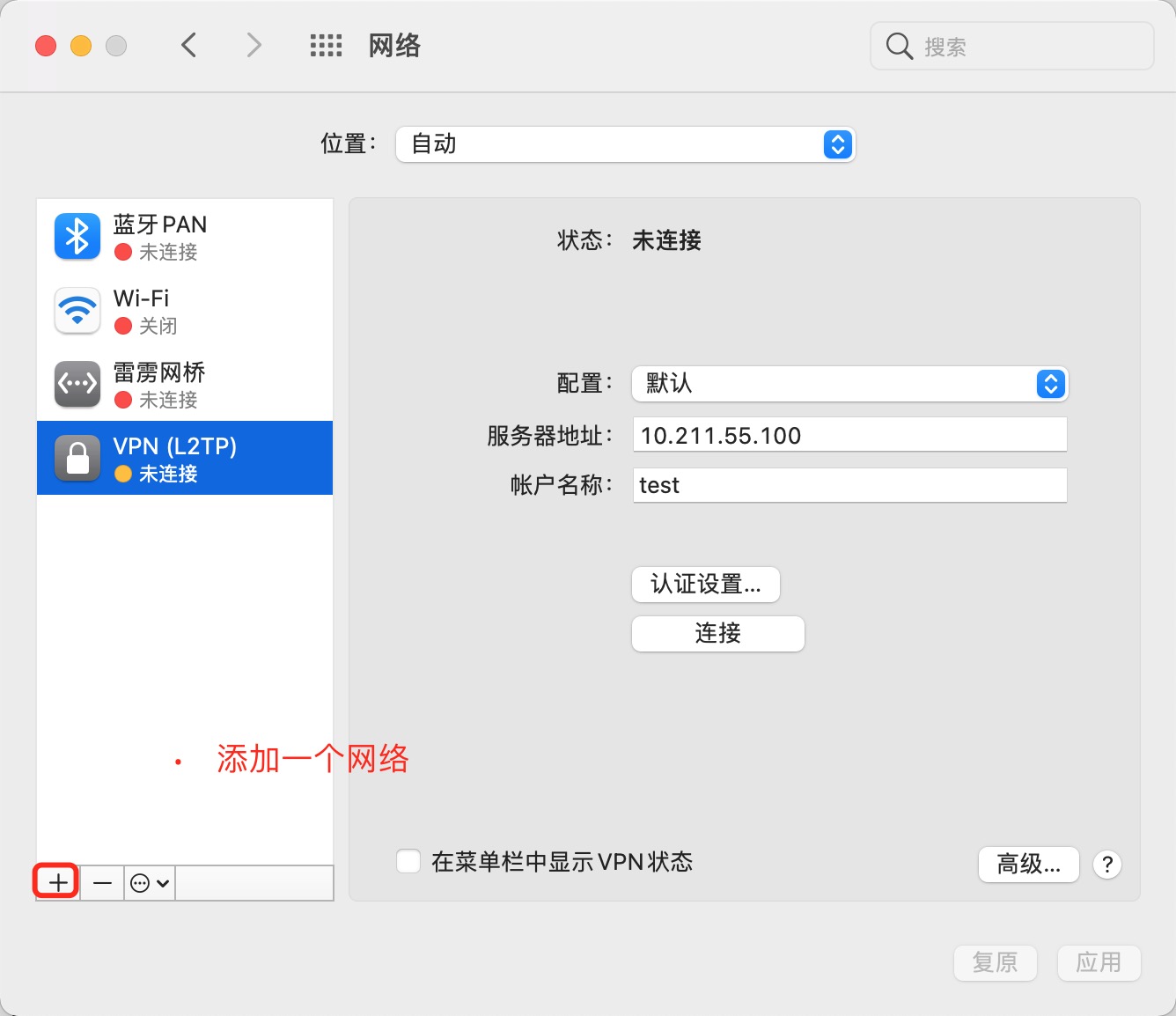
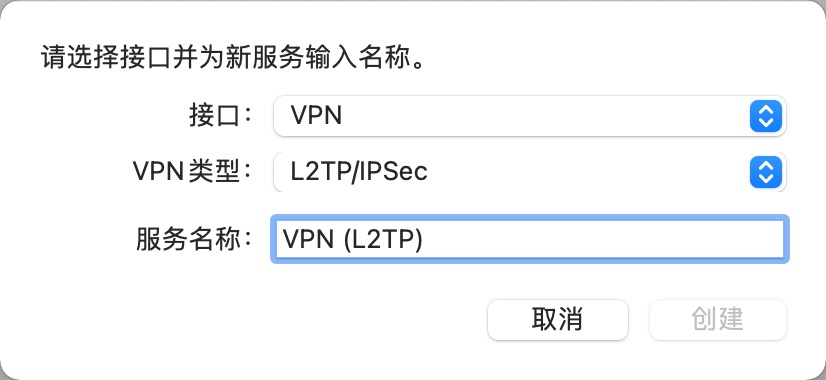
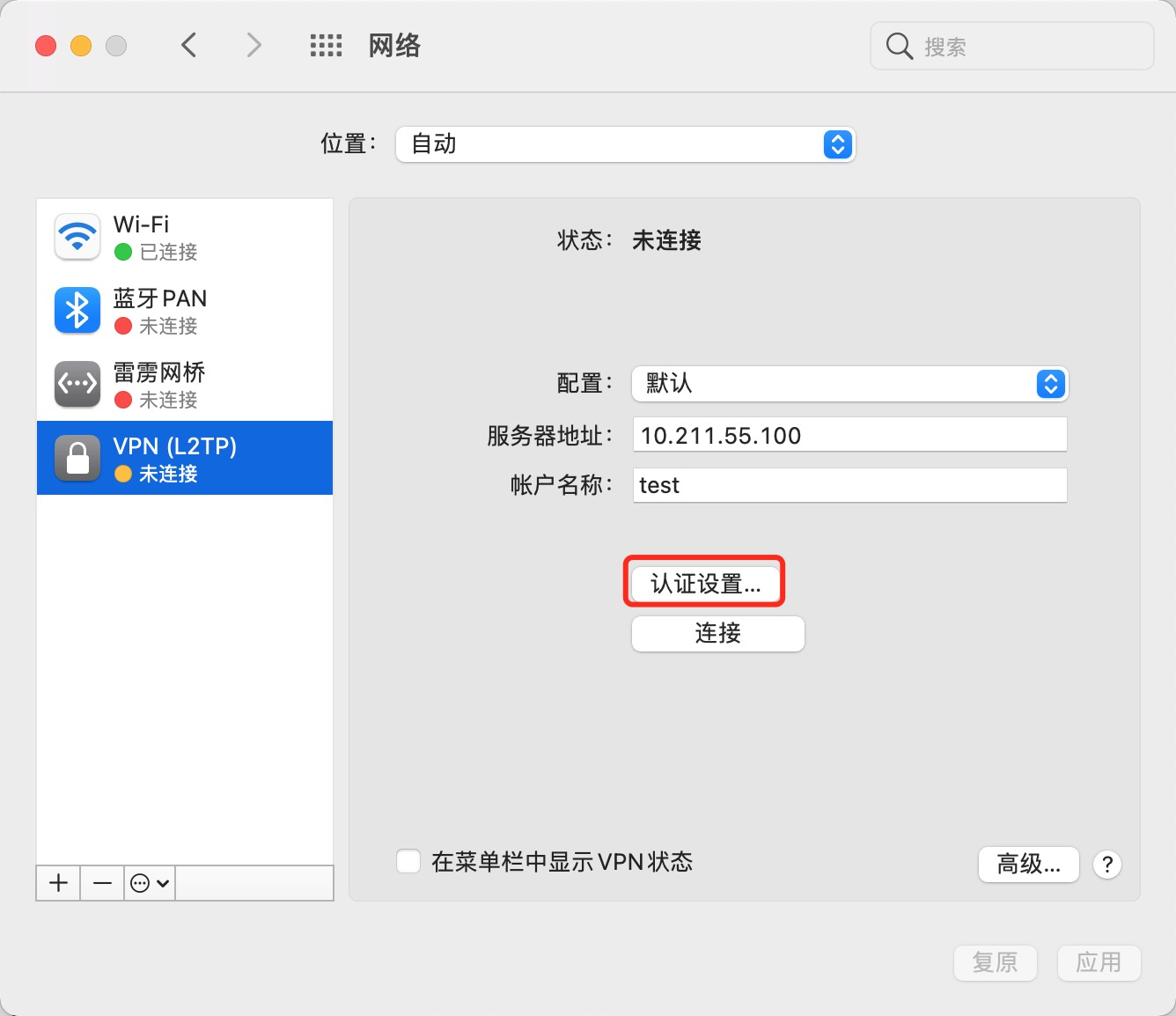
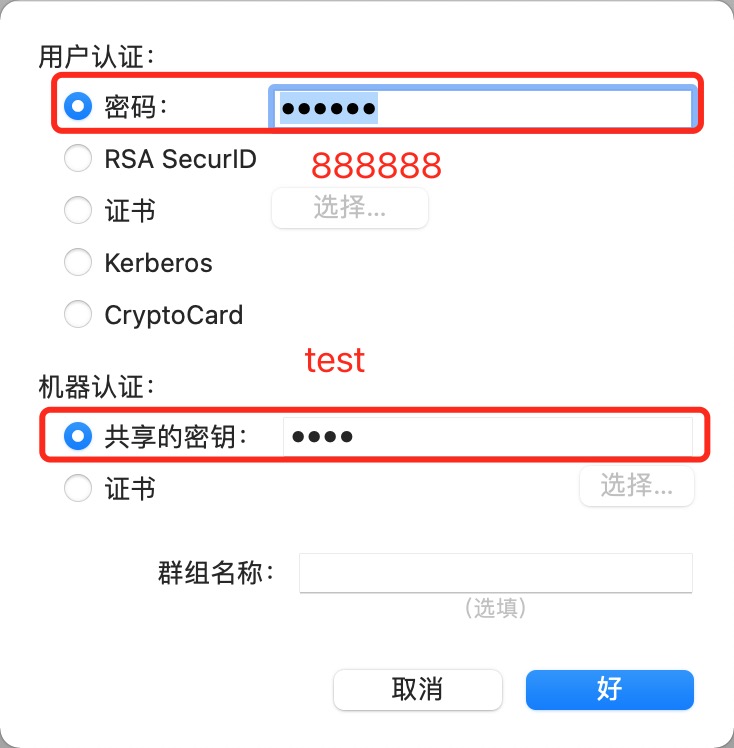
(15). mac vpn连接测试前置条件
# 1. 公享密钥为:test
# 2. 账号和密码是:test/888888
# 3. vpn:10.211.55.100
(16). mac vpn图解
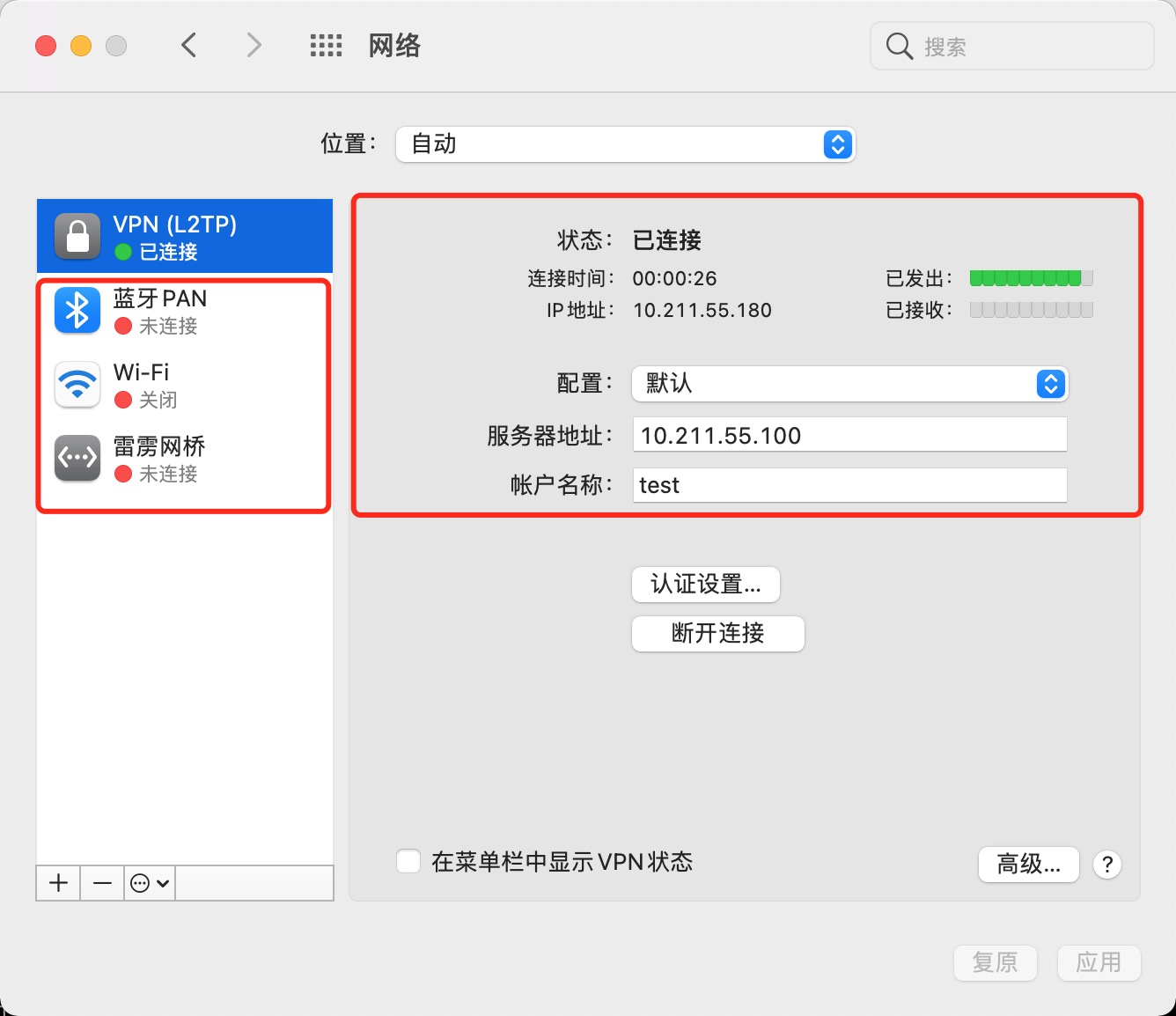
(17). 查看日志
# 1. 查看mac上的网卡信息(多了一个ppp0网卡)
lixin-macbook:~ lixin$ ifconfig
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=400<CHANNEL_IO>
ether ac:bc:32:89:41:c9
inet6 fe80::4b5:4772:eecc:1cf1%en0 prefixlen 64 secured scopeid 0x4
inet 172.17.12.223 netmask 0xffff8000 broadcast 172.17.127.255
nd6 options=201<PERFORMNUD,DAD>
media: autoselect
status: active
ppp0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1280
inet 10.211.55.180 --> 10.211.55.100 netmask 0xffff0000
# 2. 查看mac机器上连接VPN的日志内容
lixin-macbook:~ lixin$ tail -500f /var/log/ppp.log
Sat Jun 5 17:13:37 2021 : publish_entry SCDSet() failed: Success!
Sat Jun 5 17:13:37 2021 : publish_entry SCDSet() failed: Success!
Sat Jun 5 17:13:37 2021 : L2TP connecting to server '10.211.55.100' (10.211.55.100)...
Sat Jun 5 17:13:37 2021 : L2TP sent SCCRQ
Sat Jun 5 17:13:37 2021 : L2TP received SCCRP
Sat Jun 5 17:13:37 2021 : L2TP sent SCCCN
Sat Jun 5 17:13:37 2021 : L2TP sent ICRQ
Sat Jun 5 17:13:37 2021 : L2TP received ICRP
Sat Jun 5 17:13:37 2021 : L2TP sent ICCN
Sat Jun 5 17:13:37 2021 : L2TP connection established.
Sat Jun 5 17:13:37 2021 : L2TP set port-mapping for , interface: 0, protocol: 0, privatePort: 0
Sat Jun 5 17:13:37 2021 : using link 0
Sat Jun 5 17:13:37 2021 : Using interface ppp0
Sat Jun 5 17:13:37 2021 : Connect: ppp0 <--> socket[34:18]
Sat Jun 5 17:13:37 2021 : sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0x524f9485> <pcomp> <accomp>]
Sat Jun 5 17:13:37 2021 : rcvd [LCP ConfReq id=0x1 <mru 1410> <asyncmap 0x0> <auth chap MD5> <magic 0x6961214d> <pcomp> <accomp>]
Sat Jun 5 17:13:37 2021 : lcp_reqci: returning CONFACK.
Sat Jun 5 17:13:37 2021 : sent [LCP ConfAck id=0x1 <mru 1410> <asyncmap 0x0> <auth chap MD5> <magic 0x6961214d> <pcomp> <accomp>]
Sat Jun 5 17:13:37 2021 : rcvd [LCP ConfAck id=0x1 <asyncmap 0x0> <magic 0x524f9485> <pcomp> <accomp>]
Sat Jun 5 17:13:37 2021 : sent [LCP EchoReq id=0x0 magic=0x524f9485]
Sat Jun 5 17:13:37 2021 : rcvd [CHAP Challenge id=0xe4 <c8a974f4c518d1ec11774ae36226cd6d>, name = "xl2tpd"]
Sat Jun 5 17:13:37 2021 : sent [CHAP Response id=0xe4 <d396fcbac6cdab32216fa0dd79d538f6>, name = "test"]
Sat Jun 5 17:13:37 2021 : rcvd [LCP EchoRep id=0x0 magic=0x6961214d]
Sat Jun 5 17:13:37 2021 : rcvd [CHAP Success id=0xe4 "Access granted"]
Sat Jun 5 17:13:37 2021 : CHAP authentication succeeded: Access granted
Sat Jun 5 17:13:37 2021 : sent [IPCP ConfReq id=0x1 <addr 0.0.0.0> <ms-dns1 0.0.0.0> <ms-dns3 0.0.0.0>]
Sat Jun 5 17:13:37 2021 : sent [IPV6CP ConfReq id=0x1 <addr fe80::aebc:32ff:fe89:41c9>]
Sat Jun 5 17:13:37 2021 : sent [ACSCP ConfReq id=0x1 <route vers 16777216> <domain vers 16777216>]
Sat Jun 5 17:13:37 2021 : rcvd [IPCP ConfReq id=0x1 <compress VJ 0f 01> <addr 10.211.55.100>]
Sat Jun 5 17:13:37 2021 : ipcp: returning Configure-REJ
Sat Jun 5 17:13:37 2021 : sent [IPCP ConfRej id=0x1 <compress VJ 0f 01>]
Sat Jun 5 17:13:37 2021 : rcvd [LCP ProtRej id=0x2 80 57 01 01 00 0e 01 0a ae bc 32 ff fe 89 41 c9]
Sat Jun 5 17:13:37 2021 : rcvd [LCP ProtRej id=0x3 82 35 01 01 00 10 01 06 00 00 00 01 02 06 00 00 00 01]
Sat Jun 5 17:13:37 2021 : rcvd [IPCP ConfNak id=0x1 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns3 114.114.114.114>]
Sat Jun 5 17:13:37 2021 : sent [IPCP ConfReq id=0x2 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns3 114.114.114.114>]
Sat Jun 5 17:13:37 2021 : rcvd [IPCP ConfReq id=0x2 <addr 10.211.55.100>]
Sat Jun 5 17:13:37 2021 : ipcp: returning Configure-ACK
Sat Jun 5 17:13:37 2021 : sent [IPCP ConfAck id=0x2 <addr 10.211.55.100>]
Sat Jun 5 17:13:37 2021 : rcvd [IPCP ConfAck id=0x2 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns3 114.114.114.114>]
Sat Jun 5 17:13:37 2021 : ipcp: up
Sat Jun 5 17:13:37 2021 : local IP address 10.211.55.180
Sat Jun 5 17:13:37 2021 : remote IP address 10.211.55.100
Sat Jun 5 17:13:37 2021 : primary DNS address 8.8.8.8
Sat Jun 5 17:13:37 2021 : secondary DNS address 114.114.114.114
Sat Jun 5 17:13:37 2021 : Received protocol dictionaries
Sat Jun 5 17:13:37 2021 : sent [IP data <src addr 10.211.55.180> <dst addr 255.255.255.255> <BOOTP Request> <type INFORM> <client id 0x08000000010000> <parameters = 0x6 0x2c 0x2b 0x1 0xf9 0xf>]
Sat Jun 5 17:13:37 2021 : Received acsp/dhcp dictionaries
Sat Jun 5 17:13:37 2021 : Received acsp/dhcp dictionaries
Sat Jun 5 17:13:37 2021 : l2tp_wait_input: Address added. previous interface setting (name: , address: 10.211.55.2), current interface setting (name: ppp0, family: PPP, address: 10.211.55.180, subnet: 255.255.255.0, destination: 10.211.55.100).
Sat Jun 5 17:13:37 2021 : Committed PPP store on install command
Sat Jun 5 17:13:37 2021 : Committed PPP store on install command
Sat Jun 5 17:13:40 2021 : sent [IP data <src addr 10.211.55.180> <dst addr 255.255.255.255> <BOOTP Request> <type INFORM> <client id 0x08000000010000> <parameters = 0x6 0x2c 0x2b 0x1 0xf9 0xf>]
Sat Jun 5 17:13:41 2021 : L2TP port-mapping update for ignored: underlying interface down. Public Address: 0, Protocol: None, Private Port: 0, Public Port: 0
Sat Jun 5 17:13:41 2021 : L2TP port-mapping for flagged down because of no connectivity
Sat Jun 5 17:13:43 2021 : sent [IP data <src addr 10.211.55.180> <dst addr 255.255.255.255> <BOOTP Request> <type INFORM> <client id 0x08000000010000> <parameters = 0x6 0x2c 0x2b 0x1 0xf9 0xf>]
Sat Jun 5 17:13:43 2021 : Received acsp/dhcp dictionaries
Sat Jun 5 17:13:43 2021 : Committed PPP store on install command
Sat Jun 5 17:13:46 2021 : sent [IP data <src addr 10.211.55.180> <dst addr 255.255.255.255> <BOOTP Request> <type INFORM> <client id 0x08000000010000> <parameters = 0x6 0x2c 0x2b 0x1 0xf9 0xf>]
Sat Jun 5 17:13:49 2021 : sent [IP data <src addr 10.211.55.180> <dst addr 255.255.255.255> <BOOTP Request> <type INFORM> <client id 0x08000000010000> <parameters = 0x6 0x2c 0x2b 0x1 0xf9 0xf>]
Sat Jun 5 17:13:52 2021 : No DHCP server replied
# 3. 查看VPN服务器上的日志
[root@vpn-server ~]# cat /var/log/xl2tpd.log
using channel 1
Using interface ppp0
Connect: ppp0 <--> /dev/pts/2
sent [LCP ConfReq id=0x1 <mru 1410> <asyncmap 0x0> <auth chap MD5> <magic 0x6961214d> <pcomp> <accomp>]
rcvd [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0x524f9485> <pcomp> <accomp>]
sent [LCP ConfAck id=0x1 <asyncmap 0x0> <magic 0x524f9485> <pcomp> <accomp>]
rcvd [LCP ConfAck id=0x1 <mru 1410> <asyncmap 0x0> <auth chap MD5> <magic 0x6961214d> <pcomp> <accomp>]
sent [CHAP Challenge id=0xe4 <c8a974f4c518d1ec11774ae36226cd6d>, name = "xl2tpd"]
rcvd [LCP EchoReq id=0x0 magic=0x524f9485]
sent [LCP EchoRep id=0x0 magic=0x6961214d]
rcvd [CHAP Response id=0xe4 <d396fcbac6cdab32216fa0dd79d538f6>, name = "test"]
sent [CHAP Success id=0xe4 "Access granted"]
sent [IPCP ConfReq id=0x1 <compress VJ 0f 01> <addr 10.211.55.100>]
rcvd [IPCP ConfReq id=0x1 <addr 0.0.0.0> <ms-dns1 0.0.0.0> <ms-dns2 0.0.0.0>]
sent [IPCP ConfNak id=0x1 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns2 114.114.114.114>]
rcvd [IPV6CP ConfReq id=0x1 <addr fe80::aebc:32ff:fe89:41c9>]
Unsupported protocol 'IPv6 Control Protocol' (0x8057) received
sent [LCP ProtRej id=0x2 80 57 01 01 00 0e 01 0a ae bc 32 ff fe 89 41 c9]
rcvd [proto=0x8235] 01 01 00 10 01 06 00 00 00 01 02 06 00 00 00 01
Unsupported protocol 'Apple Client Server Protocol Control' (0x8235) received
sent [LCP ProtRej id=0x3 82 35 01 01 00 10 01 06 00 00 00 01 02 06 00 00 00 01]
rcvd [IPCP ConfRej id=0x1 <compress VJ 0f 01>]
sent [IPCP ConfReq id=0x2 <addr 10.211.55.100>]
rcvd [IPCP ConfReq id=0x2 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns2 114.114.114.114>]
sent [IPCP ConfAck id=0x2 <addr 10.211.55.180> <ms-dns1 8.8.8.8> <ms-dns2 114.114.114.114>]
rcvd [IPCP ConfAck id=0x2 <addr 10.211.55.100>]
found interface eth0 for proxy arp
local IP address 10.211.55.100
remote IP address 10.211.55.180
Script /etc/ppp/ip-up started (pid 5898)
Script /etc/ppp/ip-up finished (pid 5898), status = 0x0
rcvd [LCP EchoReq id=0x1 magic=0x524f9485]
sent [LCP EchoRep id=0x1 magic=0x6961214d]
rcvd [LCP EchoReq id=0x2 magic=0x524f9485]
sent [LCP EchoRep id=0x2 magic=0x6961214d]
rcvd [LCP EchoReq id=0x3 magic=0x524f9485]
sent [LCP EchoRep id=0x3 magic=0x6961214d]
rcvd [LCP EchoReq id=0x4 magic=0x524f9485]
sent [LCP EchoRep id=0x4 magic=0x6961214d]
rcvd [LCP EchoReq id=0x5 magic=0x524f9485]
sent [LCP EchoRep id=0x5 magic=0x6961214d]
